思路:
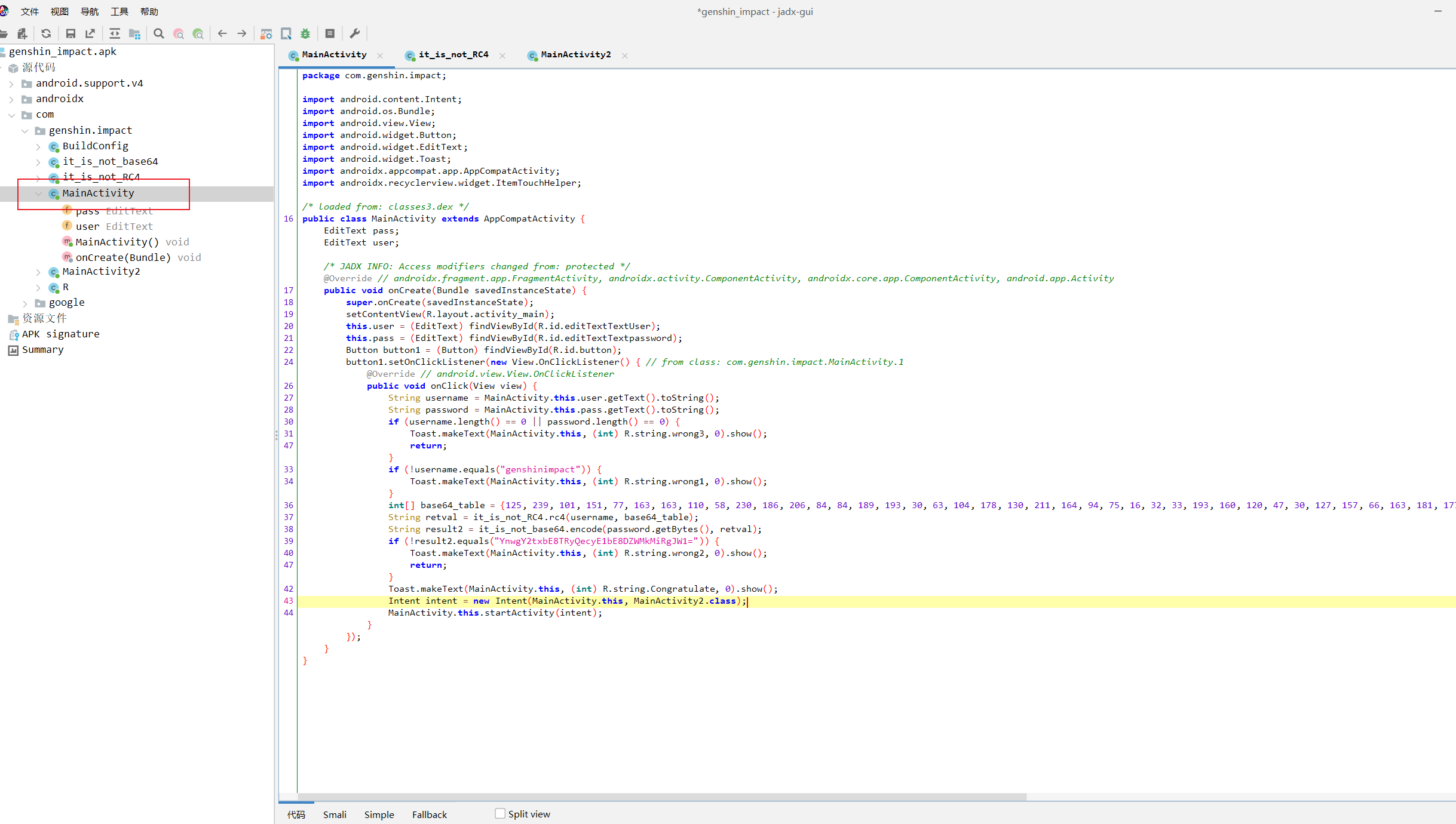
用jadx打开apk,找到主活动
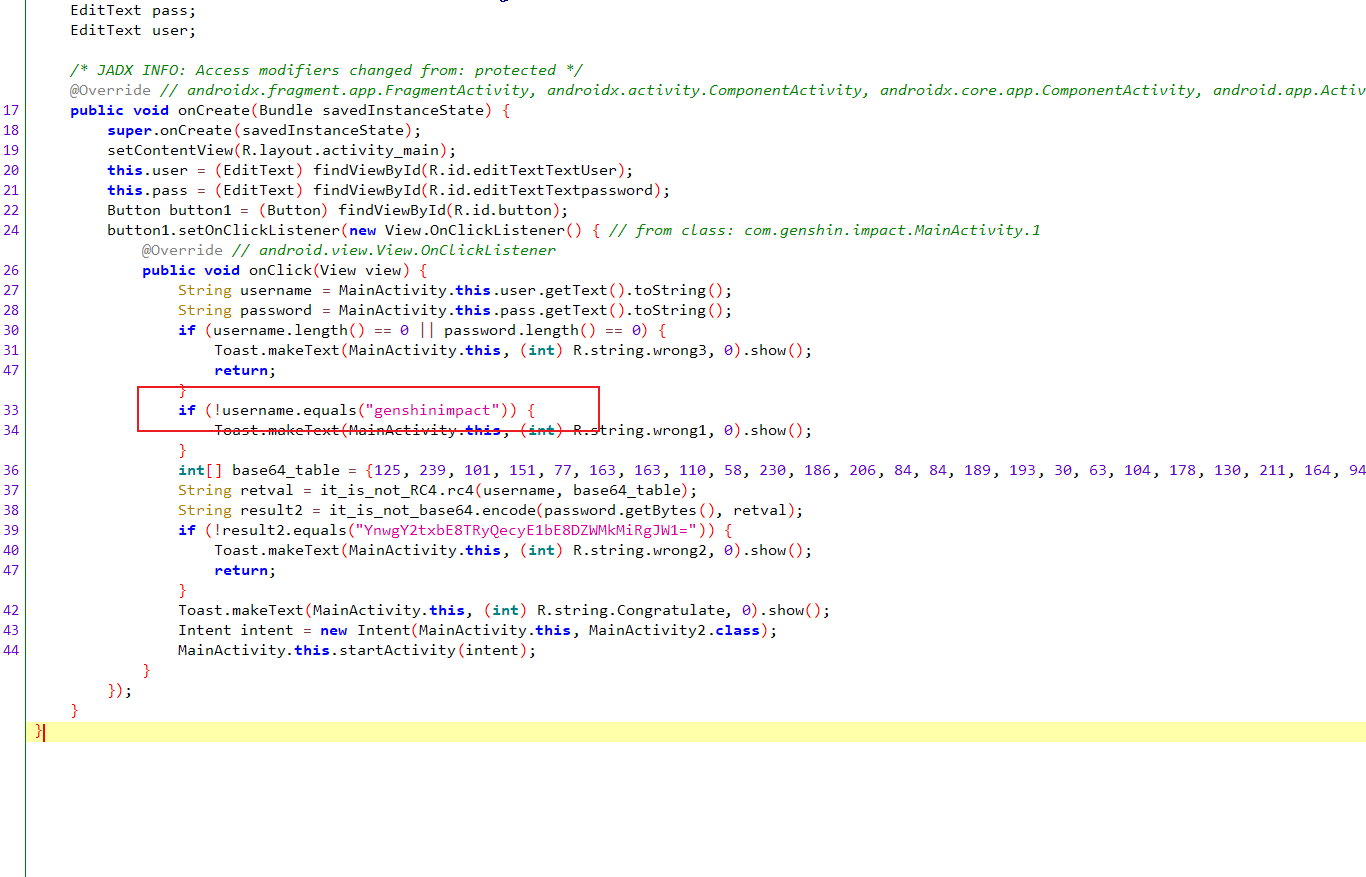
在33行判断了用户输入的username是否和genshinimpact字符串相等
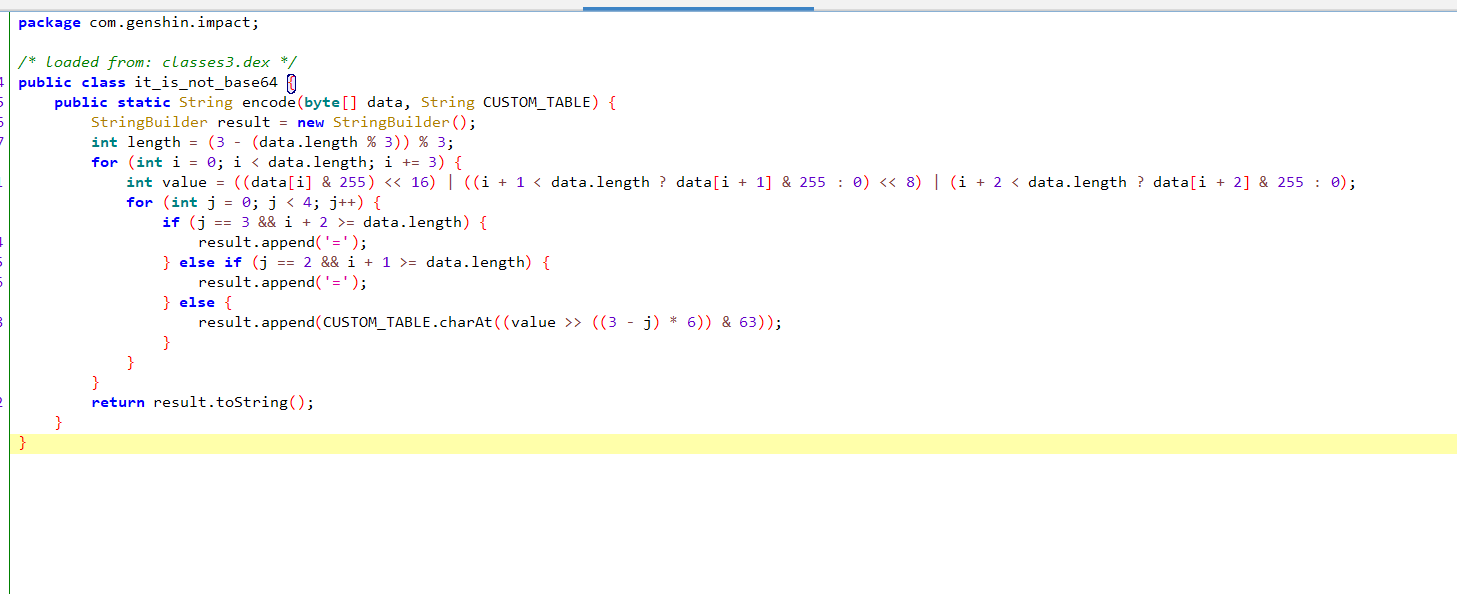
继续往下看,发现了一个名叫base64_table 的数组,猜测是base64换表
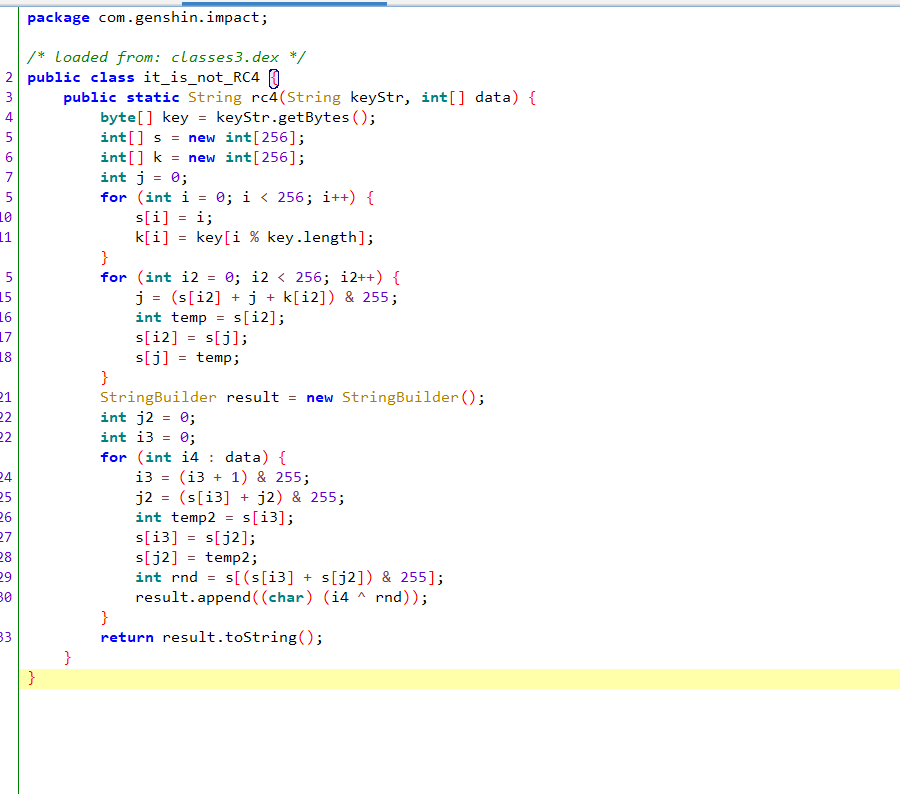
it_is_not_RC4.rc4方法对base64_table数组进行了处理 赋值给retval,跟进去查看
发现是将字符串genshinimpact作为秘钥对base64_table进行了rc4加密
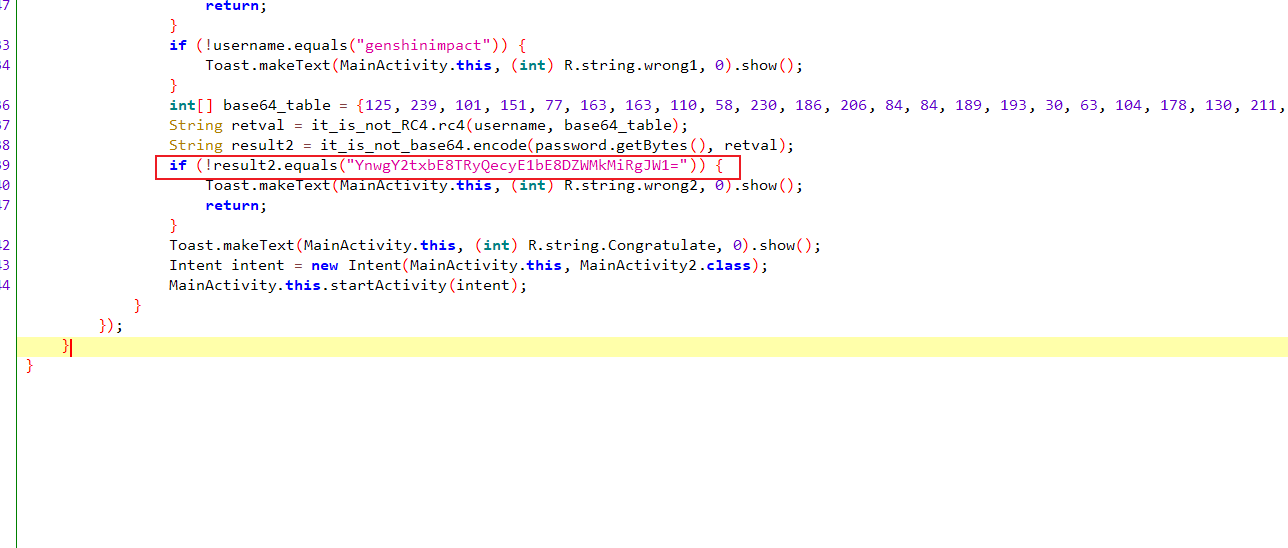
这里有个if判断力result2是否和字符串YnwgY2txbE8TRyQecyE1bE8DZWMkMiRgJW1=相等, 这个字符串就是加密的flag
result2是it_is_not_base64.encode方法的返回值,跟进去查看
发现这是个base64加密,但是把base64表换成了retval
我们只要将换的base64表解出来就能解密这个加密字符串
exp:
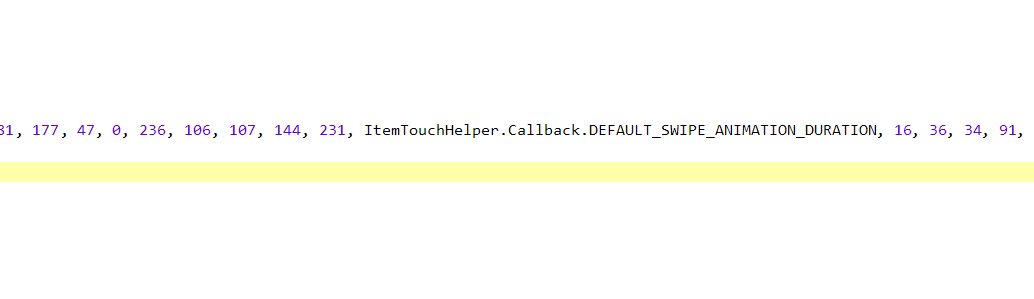
在数组中有个ItemTouchHelper.Callback.DEFAULT_SWIPE_ANIMATION_DURATION ,经过百度搜索,它的默认值是250
复制it_is_not_RC4.rc4中的加密代码,对base64_table[]进行处理
public class Main {
public static void main(String[] args) {
int[] base64_table = {125, 239, 101, 151, 77, 163, 163, 110, 58, 230, 186, 206, 84, 84, 189, 193, 30, 63, 104, 178, 130, 211, 164, 94, 75, 16, 32, 33, 193, 160, 120, 47, 30, 127, 157, 66, 163, 181, 177, 47, 0, 236, 106, 107, 144, 231, 250, 16, 36, 34, 91, 9, 188, 81, 5, 241, 235, 3, 54, 150, 40, 119, 202, 150};
String username = "genshinimpact";
String retval = it_is_not_RC4.rc4(username, base64_table);
System.out.println(retval);
}
public class it_is_not_RC4 {
public static String rc4(String keyStr, int[] data) {
byte[] key = keyStr.getBytes();
int[] s = new int[256];
int[] k = new int[256];
int j = 0;
for (int i = 0; i < 256; i++) {
s[i] = i;
k[i] = key[i % key.length];
}
for (int i2 = 0; i2 < 256; i2++) {
j = (s[i2] + j + k[i2]) & 255;
int temp = s[i2];
s[i2] = s[j];
s[j] = temp;
}
StringBuilder result = new StringBuilder();
int j2 = 0;
int i3 = 0;
for (int i4 : data) {
i3 = (i3 + 1) & 255;
j2 = (s[i3] + j2) & 255;
int temp2 = s[i3];
s[i3] = s[j2];
s[j2] = temp2;
int rnd = s[(s[i3] + s[j2]) & 255];
result.append((char) (i4 ^ rnd));
}
return result.toString();
}
}
}
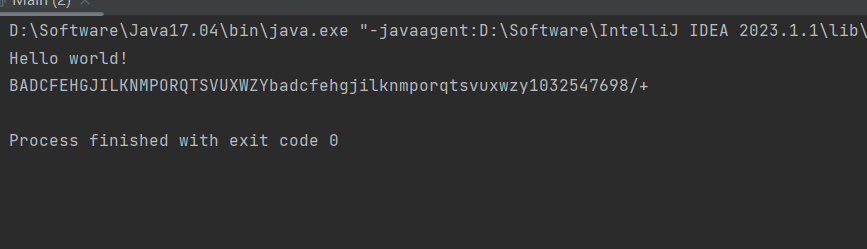
运行结果:
这就是替换的base64表
用python写脚本解密
import base64
STANDARD_ALPHABET = b'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/'
CUSTOM_ALPHABET = b'BADCFEHGJILKNMPORQTSVUXWZYbadcfehgjilknmporqtsvuxwzy1032547698/+'
ENCODE_TRANS = bytes.maketrans(STANDARD_ALPHABET, CUSTOM_ALPHABET)
DECODE_TRANS = bytes.maketrans(CUSTOM_ALPHABET, STANDARD_ALPHABET)
def encode(input):
return base64.b64encode(input).translate(ENCODE_TRANS)
def decode(input):
return base64.b64decode(input.translate(DECODE_TRANS))
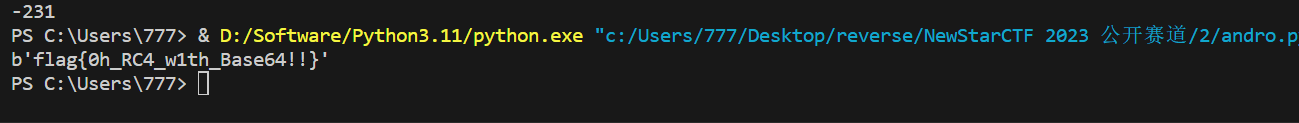
print(decode('YnwgY2txbE8TRyQecyE1bE8DZWMkMiRgJW1='))
运行结果: