思路:
64位elf,无壳
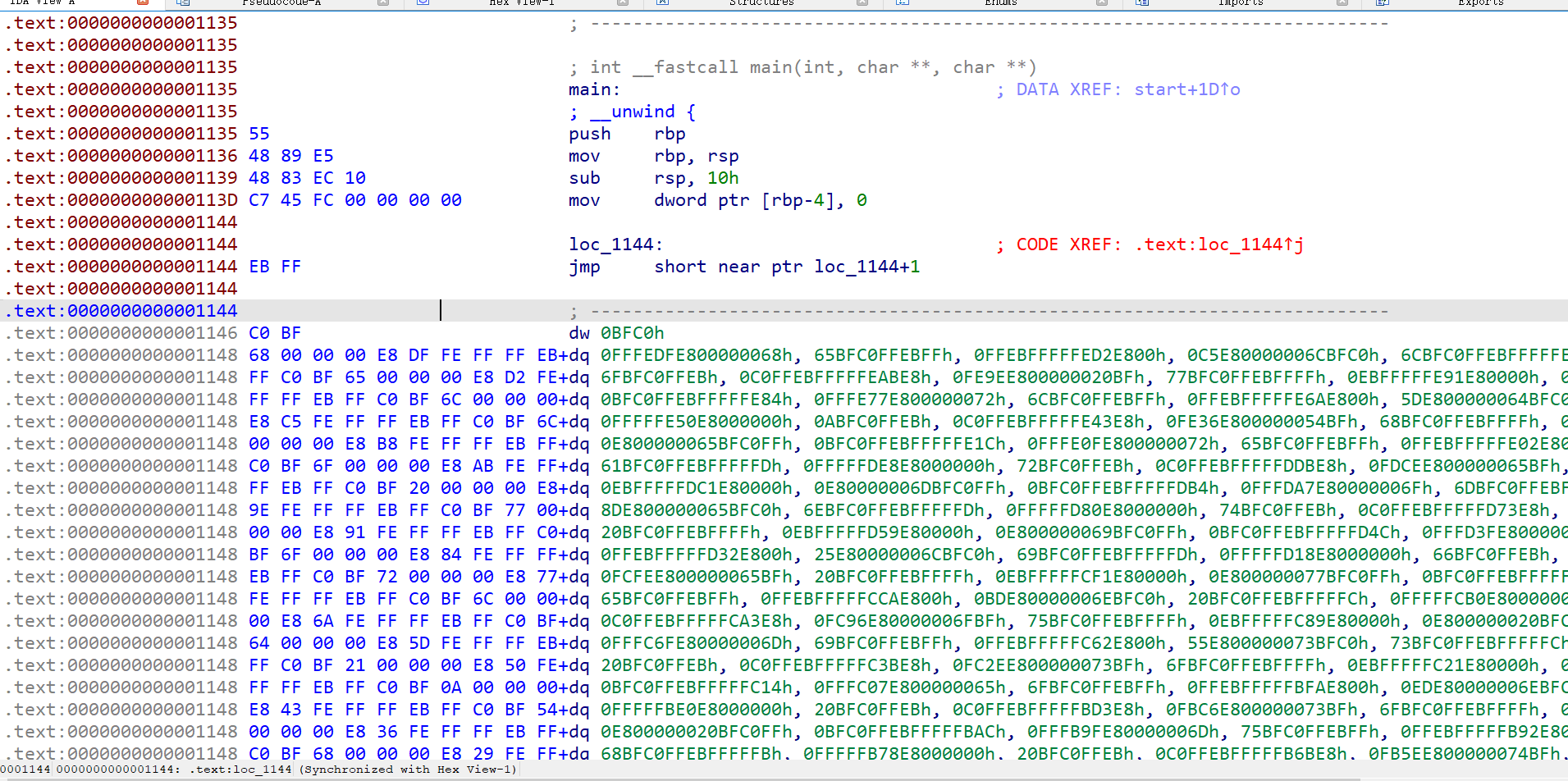
直接使用ida打开,查看主函数
映入眼帘就是一个CODE XREF和一大堆数据,这肯定是花指令
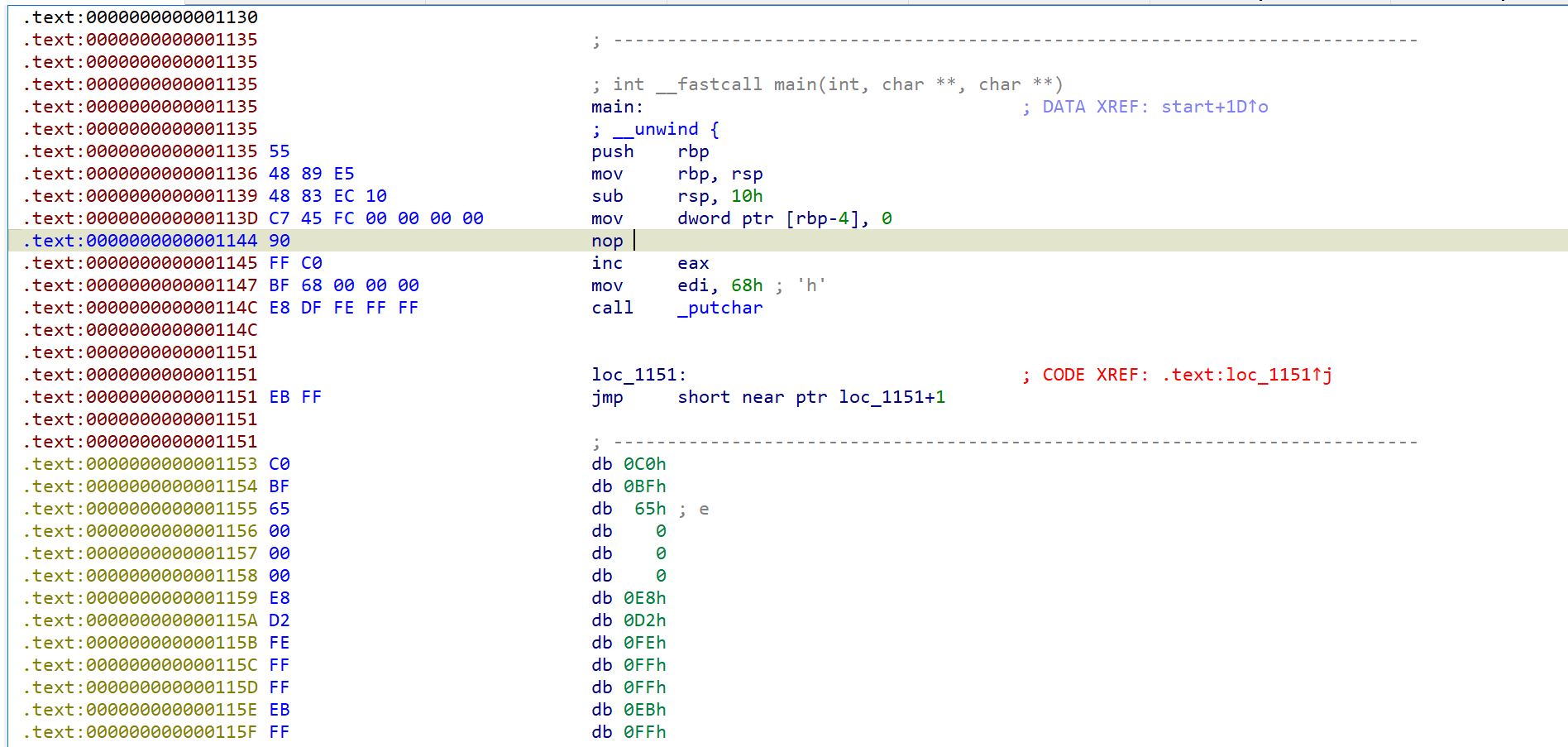
尝试去除花指令
发现有多出了一个花指令
继续重复去除花指令
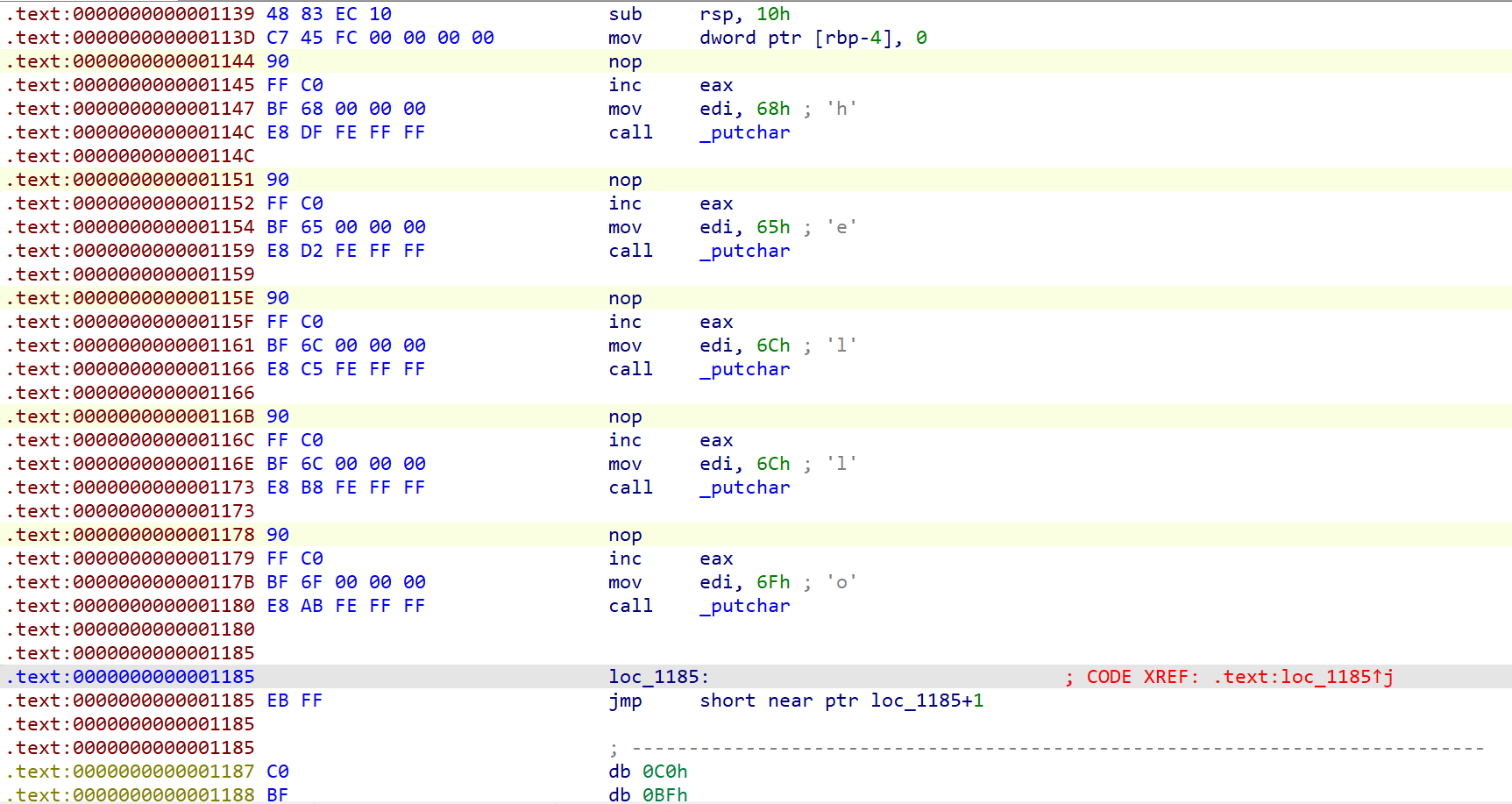
发现疑似flag的字符
这种重复的操作直接交给idapython
这些字符前面都有FF C0,写脚本通过这两个关键字找出字符
exp:
start_addr = 0x1135
end_addr = 0x3000
for i in range(start_addr, end_addr):
if ida_bytes.get_byte(i) == 0xFF and ida_bytes.get_byte(i+1) == 0xC0:
print(chr(ida_bytes.get_byte(i+3)), end="")运行结果:
hello world!
There are moments in life when you miss someone so much that you just want to pick them from your dreams and hug them for real! Dream what you want to dream;go where you want to go;be what you want to be,because you have only one life and one chance to do all the things you want to do.
May you have enough happiness to make you sweet,enough trials to make you strong,enough sorrow to keep you human,enough hope to make you happy? Always put yourself in others'shoes.If you feel that it hurts you,it probably hurts the other person, too.
GFCTF{u_are2wordy}
You find Flag, Congratulation!总结:
考点:
- 花指令
- idapython
flag:
GFCTF{u_are2wordy}