思路:
使用ida打开题目
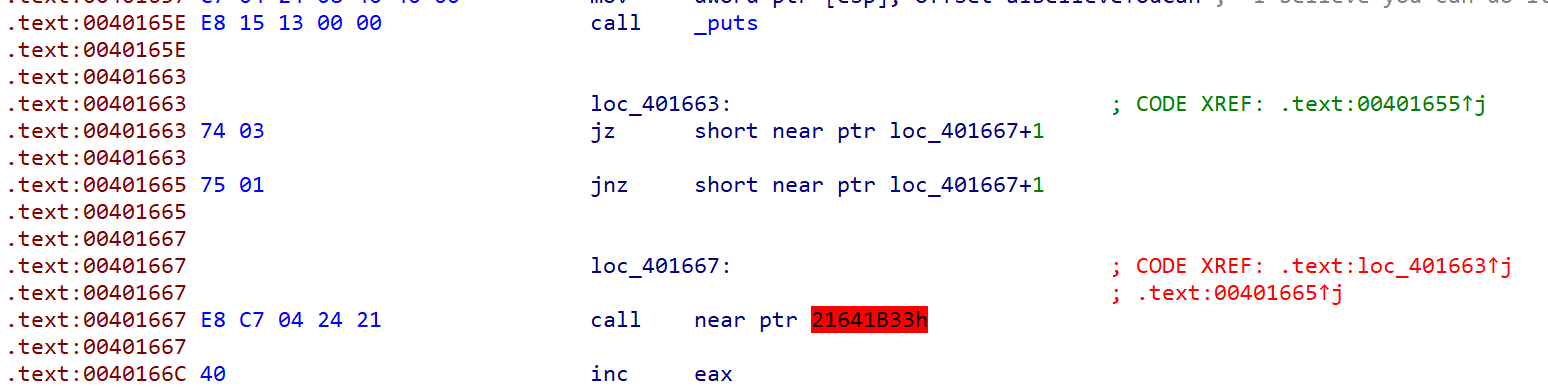
发现一片红的,ida识别不出来,根据题目确定是有花指令,向下找
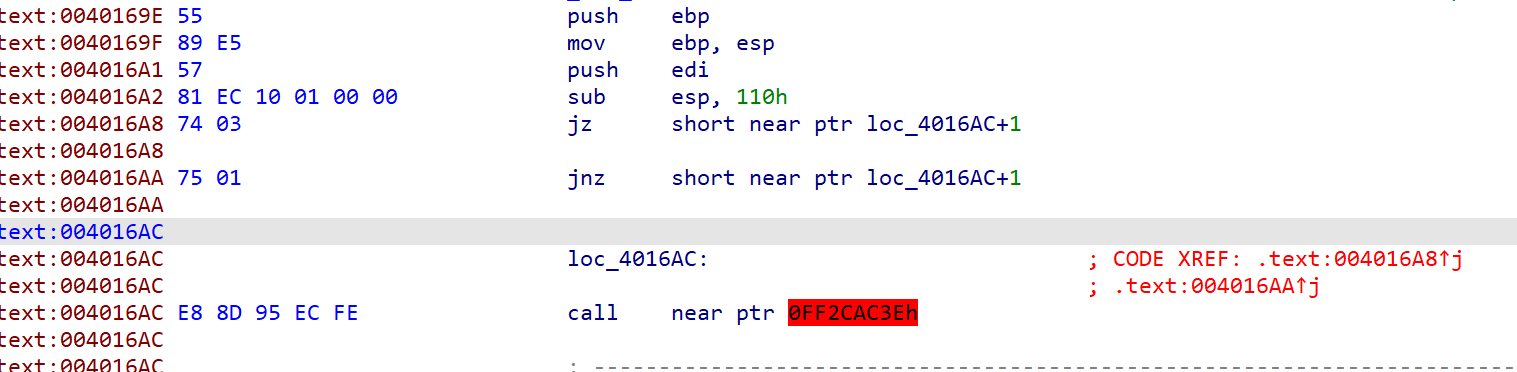
一共找到三个花指令
选中花指令跳转的地方按u,选中将不执行的代码ctrl+n,将其nop掉,再按c转换成代码,到函数头按p创建函数就完成了去花操作
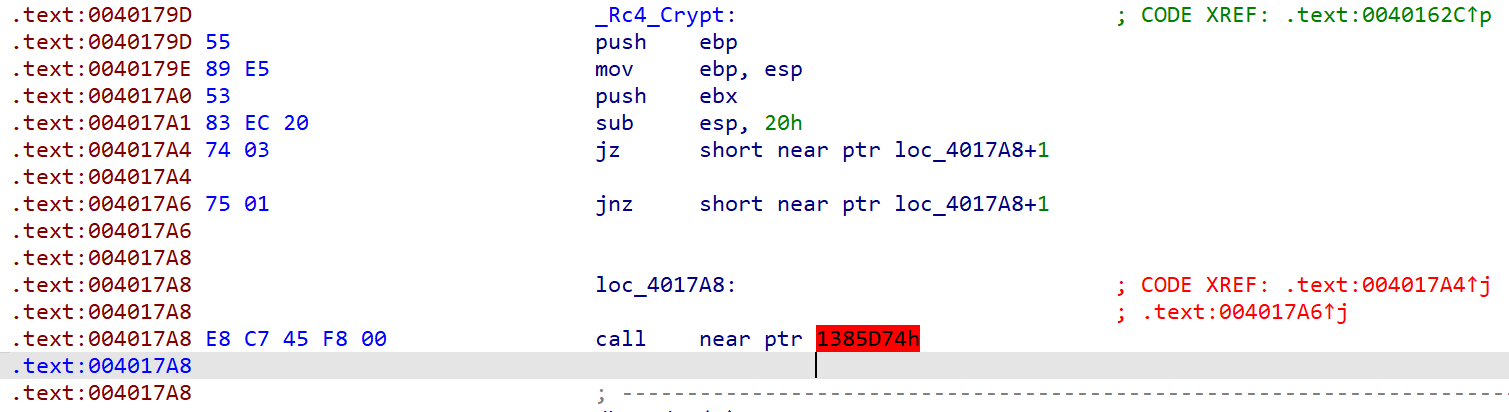
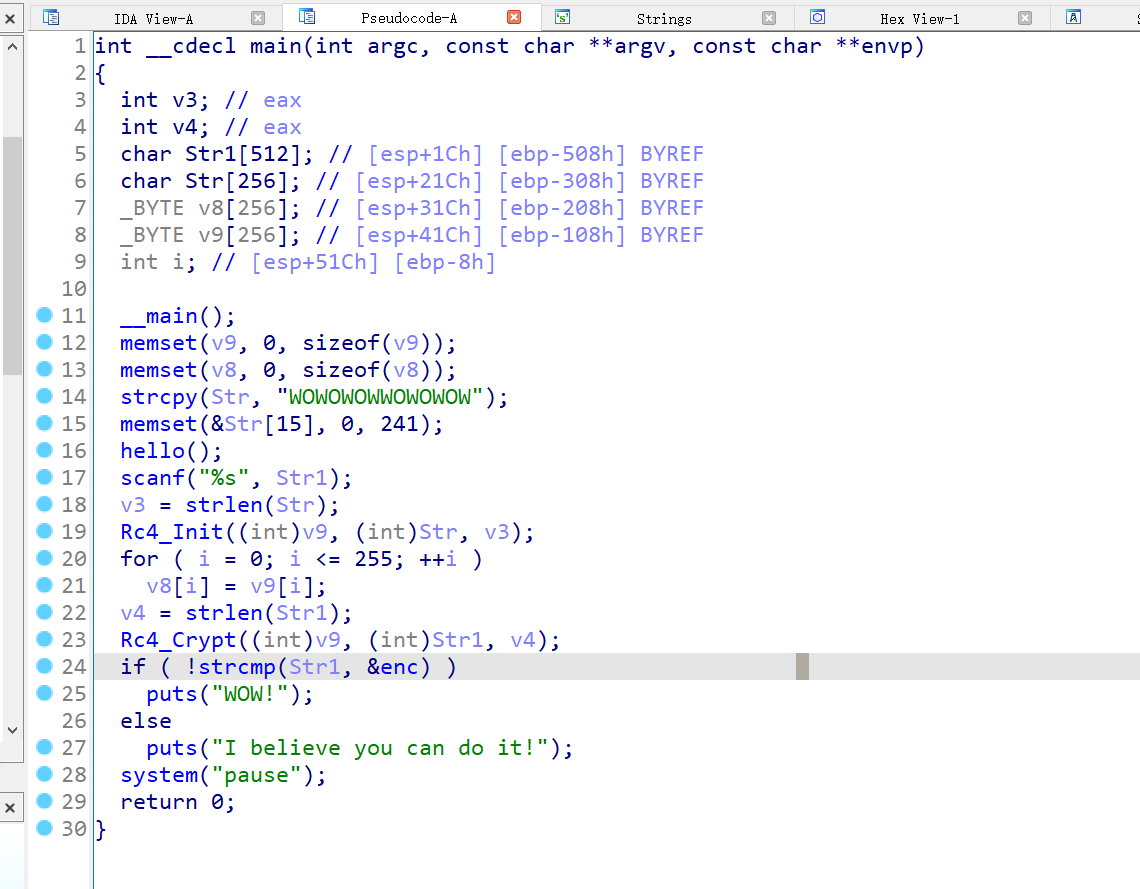
去玩花查看伪代码
发现是rc4加密,秘钥是WOWOWOWWOWOWOW
直接写脚本解密
exp:
from Crypto.Cipher import ARC4
enc = [
0xF4, 0x87, 0xD4, 0xFA, 0x61, 0xA6, 0x71, 0x12, 0x75, 0x09,
0xFE, 0xD8, 0xE4, 0x38, 0x97, 0x51, 0xA8, 0xDF, 0x85, 0x65,
0xC2, 0xB2, 0x15, 0xEF, 0x1F, 0xEC, 0x69, 0xDD, 0x6E, 0xE9,
0xCF, 0x07, 0xAE, 0xC8, 0x17, 0xF0, 0x65, 0x72, 0xE6, 0x73,
0xA4, 0x0C, 0x87, 0x64, 0x9E, 0x9E, 0x71, 0x8C, 0x7F, 0xD7,
0x75, 0x84
]
key = "WOWOWOWWOWOWOW"
rc4 = ARC4.new(key.encode())
print(rc4.decrypt(bytearray(enc)))flag:
flag{You!FlowerMaster!YouPassTheThirdPZGALAXYlevel!}